We know legacy networks require a manual configuration that’s sometimes complicated, time-consuming, and insecure. Each change presents an opportunity for human error to enter your network architecture.
To address these issues, some enterprises use intent based networking. This technology simply lets machines take care of machines, giving network administrators the time they need to design and implement the organization’s high-level desired network policy. The machine software automatically enforces the network policy and the result is a stable and secure network.
What is Intent Based Networking?
An Intent Based Networking Solution (IBNS) provides network administrators a holistic approach to network management. The creation of a network access policy is designed for the entire organization. Declaration of rules are specified to control access to the organization’s network based on user role, device, time of day, or something other than IP address.
Once defined and implemented, the system enforces the policies using a combination of advanced automation capabilities and machine learning that allows the system to evolve and adapt. This automated approach minimizes manual changes and maximizes network performance in a stable network.
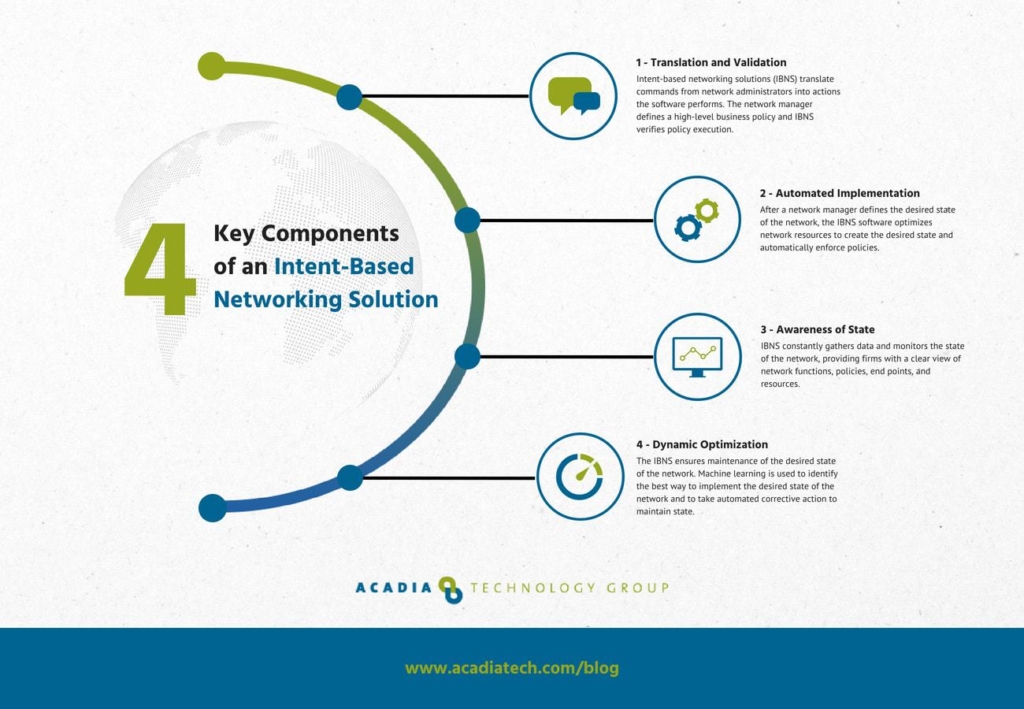
The four key components of an intent-based networking solution include:
- Translation and validation: IBNS translates commands from network administrators into actions the software performs. The network manager defines a high-level business policy they want to enforce within the network. The IBNS verifies policy execution.
- Automated implementation: After a network manager defines the desired state of the network, the IBNS software manipulates network resources to create the desired state and enforce policies.
- Awareness of state: IBNS constantly gathers data and monitors the state of the network.
- Assurance and dynamic optimization/remediation: The IBNS ensures maintenance of the desired state of the network. Machine learning is used to identify the best way to implement the desired state of the network, and it is also used to take automated corrective action to maintain state.
IBNS provides a better way to manage your network. The two primary advantages are:
- Time savings:
- Quick installation of network policy across the entire network.
- Dashboard system monitoring capabilities.
- Reduction in human error:
- Automation driven by the specified network policy reduces error while increasing security and maintaining stability.
- Machine learning provides analytics and assurance to optimize network performance and identify potential problems and threats.
Seize the Benefits of Intent-Based Networking Today
Contact Acadia Technology to obtain technical guidance from our network engineers. We provide insights into the performance of your current network and advise you on how to reduce your total cost of ownership while improving performance and productivity.
Acadia Technology Group is proud to be a Cisco Premier Partner. They will also help you learn more about the latest options for the future, including more about Cisco’s Intent Based Networking.
Cisco differentiates its IBNS using three solutions:
- Intent – automation replaces traditional time-consuming manual processes
- Context – data interpreted within the right context enhances performance, customer experience, and security
- Intuition – use of new machine learning capabilities in conjunction with Cisco’s wealth of data to drive insights and business for customers.
Cisco’s new network is built to respond quickly to the demands of your business, and it evolves as you do. It continues to learn and adapt.
- DNA Center: Dashboard to manage policy creation and provisioning, and get validation that policies are in place.
- SD Access: Software that manages automated policy enforcement and network segmentation.
- Network Data Platform: A repository that categorizes and correlates network data.
- Encrypted Traffic Analysis: Software that detects vulnerabilities through analyzes metadata of encrypted traffic.
The professionals at Acadia Technology are ready to help you complete your project on time and within the budget.

Say, you got a nice article post. Will read on…
Your writing is so refreshing and authentic It’s like having a conversation with a good friend Thank you for opening up and sharing your heart with us
… [Trackback]
[…] Read More Info here to that Topic: acadiatech.com/blog/intent-based-networking-positioned-to-transform-the-it-industry/ […]
… [Trackback]
[…] Find More to that Topic: acadiatech.com/blog/intent-based-networking-positioned-to-transform-the-it-industry/ […]
… [Trackback]
[…] Information on that Topic: acadiatech.com/blog/intent-based-networking-positioned-to-transform-the-it-industry/ […]
… [Trackback]
[…] Information to that Topic: acadiatech.com/blog/intent-based-networking-positioned-to-transform-the-it-industry/ […]